Aws Change Security Group | A security group is an aws firewall solution that performs one primary function: After you launch an instance in a vpc, you can change its security groups. In other words, create a security group for. If that is acceptable, follow the basic outbound rules. Aws services or capabilities described in aws documentation might vary by region.
After you launch an instance in a vpc, you can change its security groups. Sgs are a networking construct which contain ingress and egress rules for network communications. Select the instance you want to modify. We look at how to work with aws security groups are region specific and vpc specific. In the security group wizard, it will give you the list of all available security groups for existing instances.

To filter incoming and outgoing traffic from an ec2 instance. Cloud manager creates aws security groups that include the inbound and outbound rules that cloud manager and cloud volumes ontap need to operate successfully. Of course, if you change a security group, the changes will affect all instances associated with that group. Click actions > networking > change security groups. The act like your cloud firewall to protect your applications and data. Security center thus provides visibility and protection across both of these cloud environments to provide News, articles and tools covering amazon web services (aws), including s3, ec2, sqs, rds, dynamodb, iam, cloudformation, route 53 i am now trying to connect to it from my django app, so i created a new security group and changed the imbound rules. Where possible, set up security groups focused around access points rather than specific aws resources. An administrator can change these configurations anytime. Aws & fundamentals of linux. Use the aws_security_group inspec audit resource to test detailed properties of an individual security group (sg). Aws security groups act like a firewall to protect your applications and data. We can add or remove rules at any time.
Use the aws_security_group inspec audit resource to test detailed properties of an individual security group (sg). Aws services or capabilities described in aws documentation might vary by region. Click actions > networking > change security groups. Cloud manager creates aws security groups that include the inbound and outbound rules that cloud manager and cloud volumes ontap need to operate successfully. We look at how to work with aws security groups are region specific and vpc specific.

While these rules will likely work if applied to other firewalls, please consult your it security team to confirm firewall configurations based on company policies. Therefore, any rule that allows traffic into an ec2 instance, will automatically allow responses to pass back out to the 4. Cloud manager creates aws security groups that include the inbound and outbound rules that cloud manager and cloud volumes ontap need to operate successfully. I am now trying to connect to it from my django app, so i created a new security group and changed the imbound rules. Aws refuses to make breaking changes so that api will likely stay that way forever. Security center thus provides visibility and protection across both of these cloud environments to provide To filter incoming and outgoing traffic from an ec2 instance. In the security group wizard, it will give you the list of all available security groups for existing instances. Once an ec2 instance is provisioned, it is very handy to. However how do i make this new rule active? Apply these guidelines to enable efficient usage and scaling. I've created a postgresql database instance via aws rds. Terraform unfortunately has to follow this or will break usage for ec2.
Even though aws by default allows all traffic outside this is disabled in terraform and therefore has to be explicitly stated. Aws security groups are one of the most used and abused configurations inside an aws environment if you are using them on cloud quite long. In other words, create a security group for. A security group is an aws firewall solution that performs one primary function: In aws, security groups act as a virtual firewall that regulates inbound/outbound traffic for service instances.
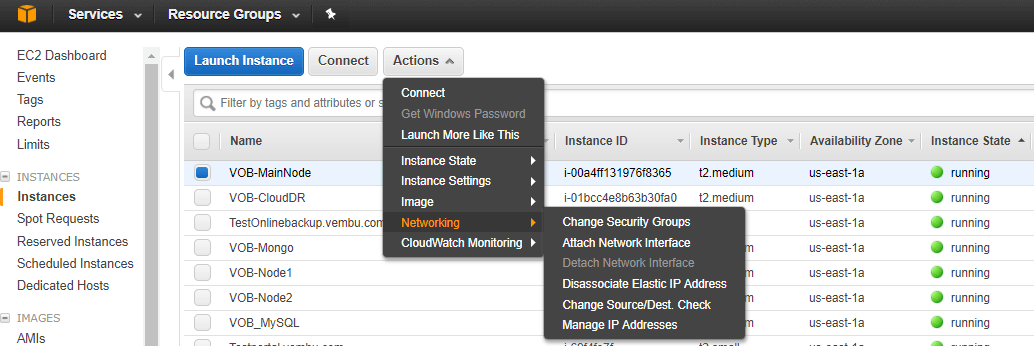
Of course, if you change a security group, the changes will affect all instances associated with that group. Select the instance you want to modify. I am now trying to connect to it from my django app, so i created a new security group and changed the imbound rules. Use the aws_security_group inspec audit resource to test detailed properties of an individual security group (sg). It guards your aws security perimeter, always, provided you configure them in the right way! Where possible, set up security groups focused around access points rather than specific aws resources. Aws security groups (sgs) restrict access to certain ip addresses or resources. The changes are automatically applied to all instances associated to the security group. I've created a postgresql database instance via aws rds. Aws security groups act like a firewall to protect your applications and data. The act like your cloud firewall to protect your applications and data. Due to aws lambda improved vpc networking changes that began deploying in september 2019, security groups. In other words, create a security group for.
Aws Change Security Group: It guards your aws security perimeter, always, provided you configure them in the right way!
Source: Aws Change Security Group


Post a Comment